Real Time Data & Insight For Your Buildings, People and Contractors
Verified is a market-leading, data-driven platform, providing real time insight for visitor, contractor and safety management
Verified is a market-leading, data-driven platform, providing real time insight for visitor, contractor and safety management














Verified’s advanced QR code and web-based workflow gives you increased accuracy, greater control and visibility
Verified's visitor management platform screens, validates and monitors any person accessing locations and sites via contactless sign-in.
Verified provides a broad range of modules that make it easy for you to have real-time visibility, control and verification of all maintenance tasks across your property portfolio.
Optimised role and site specific safety/induction workflow to manage risk, ensure compliance and currency of contractor certification.
Verified leverages advanced SaaS based technology, ensures easy deployment and accessibility for your business
Accurate data that you own, unified in a single cloud location and available 24/7
Deep site analytics via customisable reporting and management tools
Accurate information to capture audit trails, ensuring risk minimisation and regulatory compliance
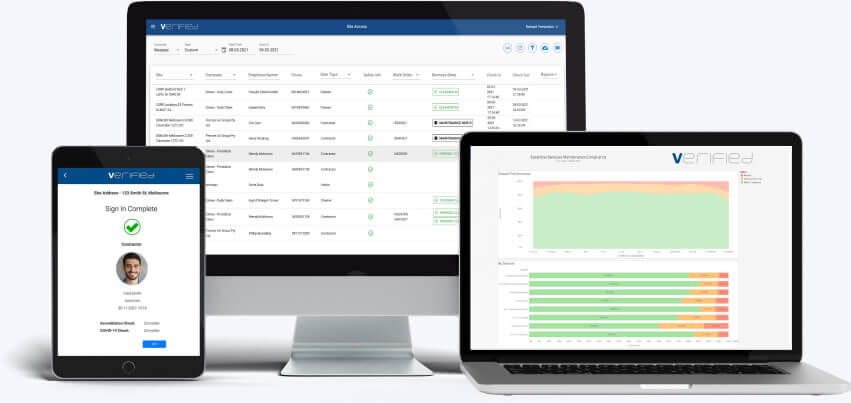
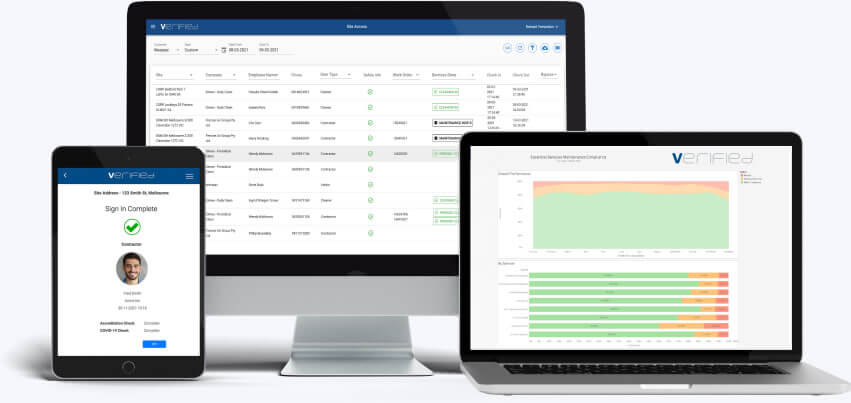
Over the past 20 years, Verified has delivered significant cost savings, greater
transparency and process optimisation for Australia’s leading companies.
With 20 years’ experience in the business, we believe in sharing our expertise on workplace safety,
compliance and transparency throughout the workplace.
The Key to Complete Visibility for Your Business Data ownership extends well beyond legal entitlements – it shapes the foundation of both day-to-day operations…
A New Look & Instant Verification Checks Check out the latest enhancements at Verified, from user interface improvements to real-time on-site verification capabi…
Elevating System Efficiency: Our Focus On User Experience Success in modern day site management involves turning everyday complexity into intuitive simplicity. With …
Invisible Services, Visible Costs: Paying For What You Receive Businesses continue to have ineffective contract visibility on the services being delivered by their �…


Experience has been second to none. Customer Service is better than excellent with our Account Manager only a call away and always ready to help like a true partner.

The system primarily helps us to stay on top of ensuring our scheduled regulatory compliance maintenance activities across a number of sites are being completed.

Extremely professional, supportive and accommodating in ensuring the system is fit for purpose for our business.

Verified is very easy to work with and are open to exploring new ways of working and using the technology.

I’ve been waiting for 10 years for something like this. We had 100% compliance on paper and no understanding of who was in a site at any particular time.

The benefit is the data. It gives me peace of mind that I am compliant and can prove it.

Makes contractors accountable to complete the work per their schedules and in line with Australian Standards. We use it daily.